Terraform으로 Azure에 VM 인스턴스를 하나 생성해보자. 사실 생각보다 간단하지 않고, 생성해야 할 리소스가 꽤 많다.
- Resource Group
- Virtual Network
- Subnet
- Public IP
- Network Security Group 및 Rule
- Network Interface 및 Association
- Boot diagnostics 저장을 위한 Storage Account
- SSH Key
- VM Instance
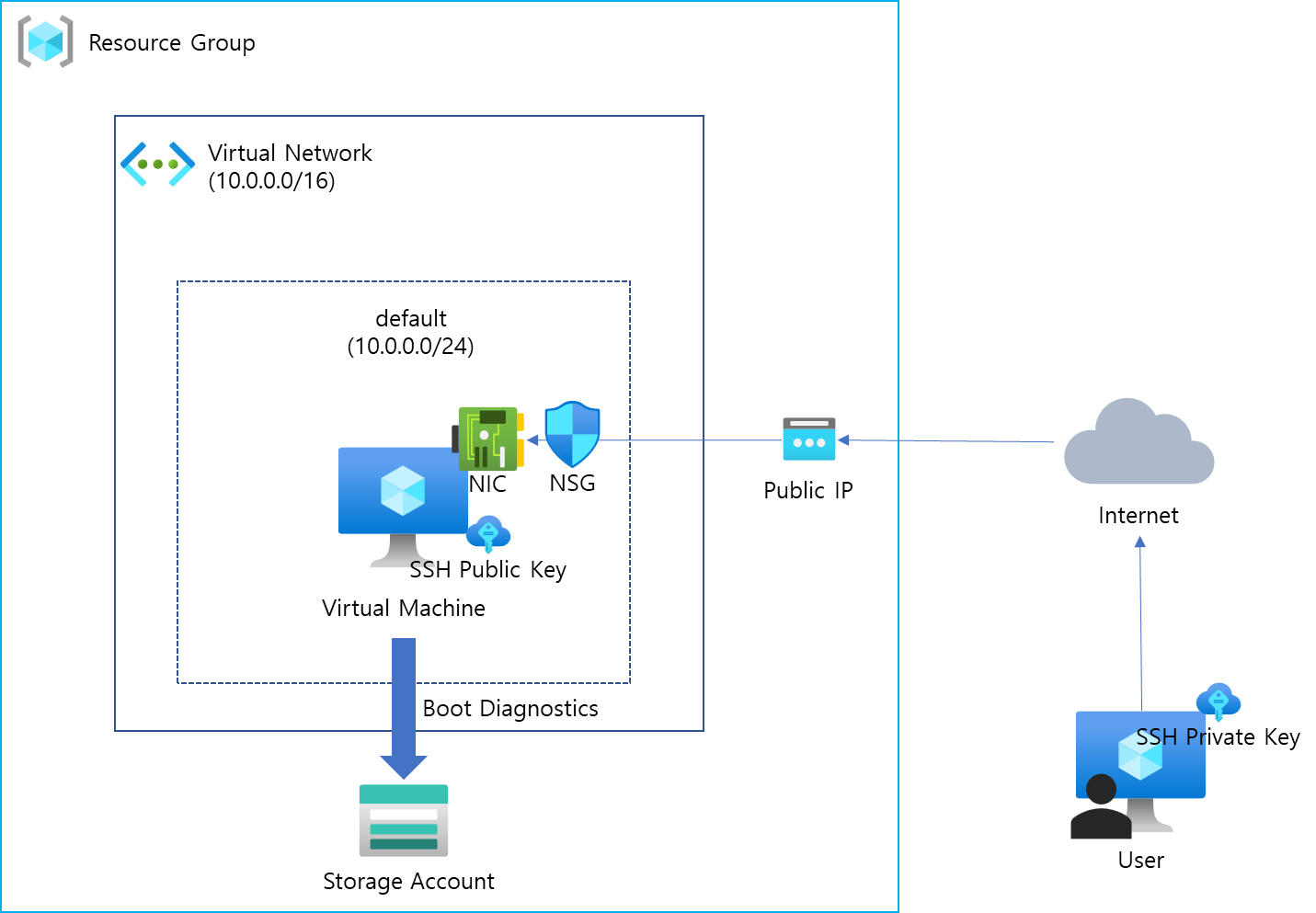
위에서 나열한 리소스들을 다이어그램으로 표현하면 다음과 같다.
1. Terraform을 실행할 Directory를 생성한다.
mkdir demo-vm && cd demo-vm2. 아래와 같이 main.tf 파일을 작성한다.
# Configure the Microsoft Azure Provider
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~>2.0"
}
}
}
provider "azurerm" {
features {}
}
# Create a resource group if it doesn't exist
resource "azurerm_resource_group" "myterraformgroup" {
name = "myResourceGroup"
location = "koreacentral"
tags = {
environment = "Terraform Demo"
}
}
# Create virtual network
resource "azurerm_virtual_network" "myterraformnetwork" {
name = "myVnet"
address_space = ["10.0.0.0/16"]
location = "koreacentral"
resource_group_name = azurerm_resource_group.myterraformgroup.name
tags = {
environment = "Terraform Demo"
}
}
# Create subnet
resource "azurerm_subnet" "myterraformsubnet" {
name = "mySubnet"
resource_group_name = azurerm_resource_group.myterraformgroup.name
virtual_network_name = azurerm_virtual_network.myterraformnetwork.name
address_prefixes = ["10.0.0.0/24"]
}
# Create public IPs
resource "azurerm_public_ip" "myterraformpublicip" {
name = "myPublicIP"
location = "koreacentral"
resource_group_name = azurerm_resource_group.myterraformgroup.name
allocation_method = "Dynamic"
tags = {
environment = "Terraform Demo"
}
}
output "vm_public_ip" {
value = "${azurerm_public_ip.myterraformpublicip.*.ip_address}"
}
# Create Network Security Group and rule
resource "azurerm_network_security_group" "myterraformnsg" {
name = "myNetworkSecurityGroup"
location = "koreacentral"
resource_group_name = azurerm_resource_group.myterraformgroup.name
security_rule {
name = "SSH"
priority = 1001
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "22"
source_address_prefix = "*"
destination_address_prefix = "*"
}
tags = {
environment = "Terraform Demo"
}
}
# Create network interface
resource "azurerm_network_interface" "myterraformnic" {
name = "myNIC"
location = "koreacentral"
resource_group_name = azurerm_resource_group.myterraformgroup.name
ip_configuration {
name = "myNicConfiguration"
subnet_id = azurerm_subnet.myterraformsubnet.id
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.myterraformpublicip.id
}
tags = {
environment = "Terraform Demo"
}
}
# Connect the security group to the network interface
resource "azurerm_network_interface_security_group_association" "example" {
network_interface_id = azurerm_network_interface.myterraformnic.id
network_security_group_id = azurerm_network_security_group.myterraformnsg.id
}
# Generate random text for a unique storage account name
resource "random_id" "randomId" {
keepers = {
# Generate a new ID only when a new resource group is defined
resource_group = azurerm_resource_group.myterraformgroup.name
}
byte_length = 8
}
# Create storage account for boot diagnostics
resource "azurerm_storage_account" "mystorageaccount" {
name = "diag${random_id.randomId.hex}"
resource_group_name = azurerm_resource_group.myterraformgroup.name
location = "koreacentral"
account_tier = "Standard"
account_replication_type = "LRS"
tags = {
environment = "Terraform Demo"
}
}
# Create (and display) an SSH key
resource "tls_private_key" "example_ssh" {
algorithm = "RSA"
rsa_bits = 4096
}
output "tls_private_key" {
value = tls_private_key.example_ssh.private_key_pem
sensitive = true
}
# Create virtual machine
resource "azurerm_linux_virtual_machine" "myterraformvm" {
name = "myVM"
location = "koreacentral"
resource_group_name = azurerm_resource_group.myterraformgroup.name
network_interface_ids = [azurerm_network_interface.myterraformnic.id]
size = "Standard_DS1_v2"
os_disk {
name = "myOsDisk"
caching = "ReadWrite"
storage_account_type = "Premium_LRS"
}
source_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "18.04-LTS"
version = "latest"
}
computer_name = "myvm"
admin_username = "azureuser"
disable_password_authentication = true
admin_ssh_key {
username = "azureuser"
public_key = tls_private_key.example_ssh.public_key_openssh
}
boot_diagnostics {
storage_account_uri = azurerm_storage_account.mystorageaccount.primary_blob_endpoint
}
tags = {
environment = "Terraform Demo"
}
}3. Terraform 명령어를 실행한다.
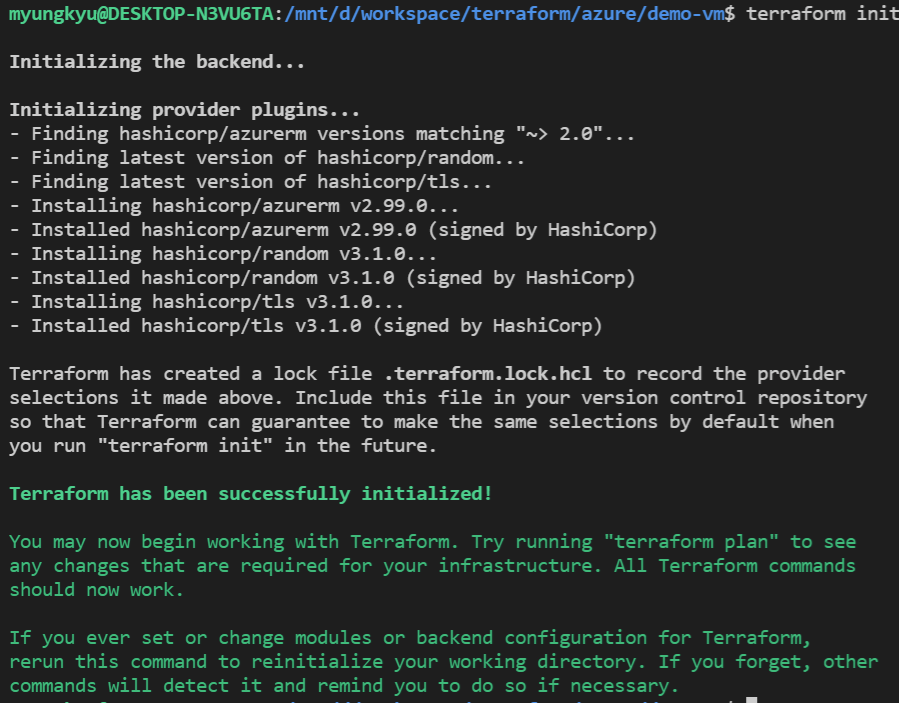
terraform init
terraform plan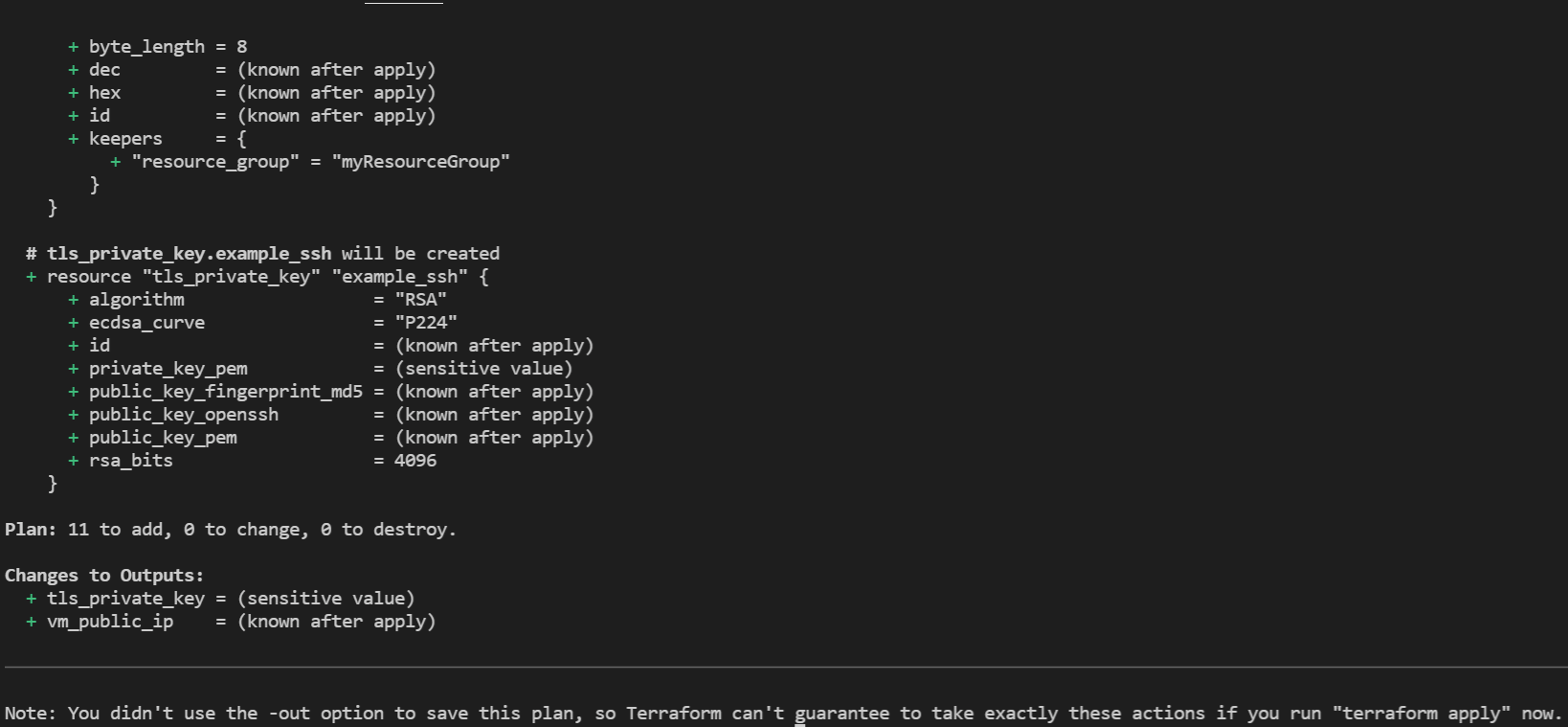
terraform apply -auto-approve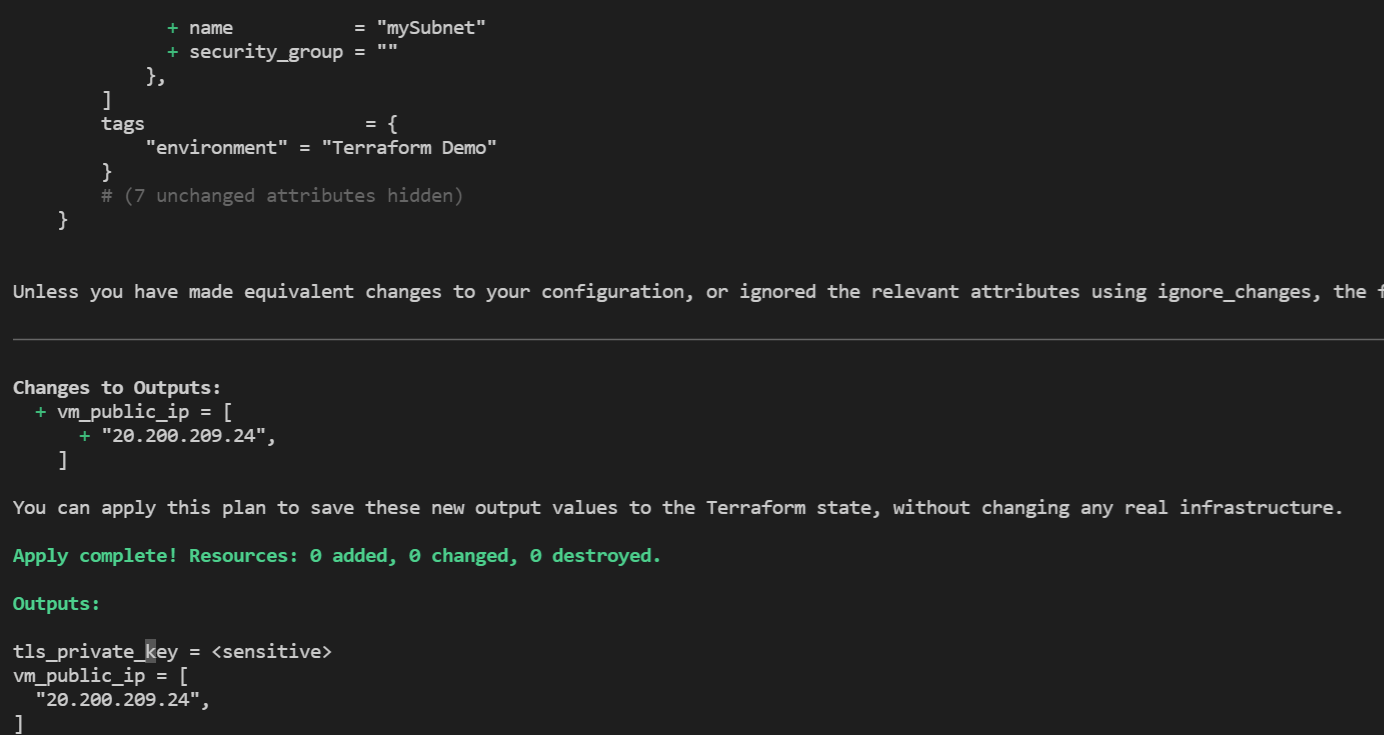
아래 명령어를 통해 SSH Private Key를 파일로 저장할 수 있다.
terraform output -raw tls_private_key > demo-vm-private-key
chmod 400 demo-vm-private-key
ssh로 VM에 연결이 가능한지 확인한다. VM의 Public IP Address는 'terraform apply' 명령어의 결과로 알 수 있다.
ssh -i demo-vm-private-key azureuser@<public ip addrress>
실습이 끝났으므로 모든 리소스를 삭제한다.
terraform destroy -auto-approve참고
Configure a Linux VM with infrastructure in Azure using Terraform
'IaC' 카테고리의 다른 글
| Terraform - Kubernetes 연동 (0) | 2022.06.05 |
|---|---|
| Terraform - Azure(2) (0) | 2022.03.13 |
| Terraform - Azure(1) (0) | 2022.03.11 |
| Terraform - (7) Advanced (1) | 2021.06.19 |
| Terraform - (6) IAM (0) | 2021.06.18 |